Introducing
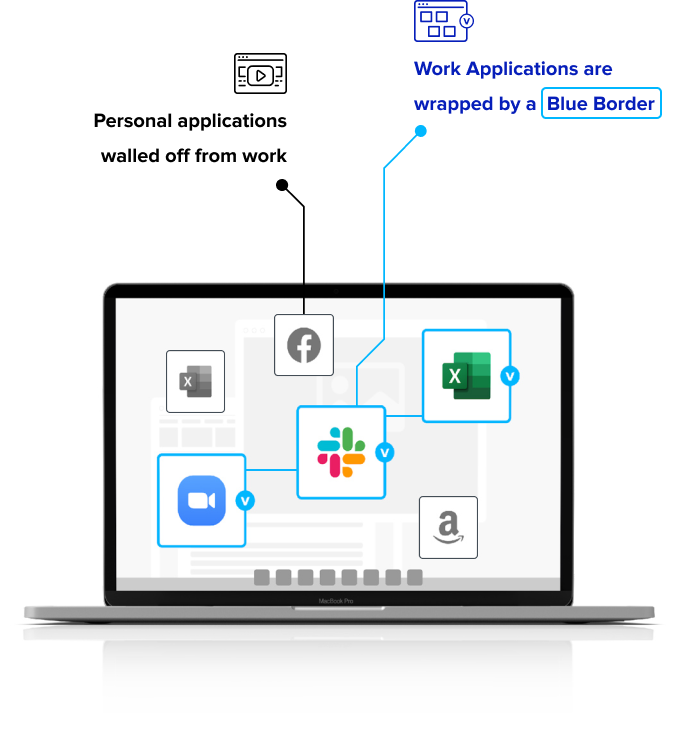
The Blue Border™ secures remote work without managing the entire computer
With Venn, work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the enclave – visually indicated by the Blue Border™ – where business activity is isolated and protected from any personal use on the same computer.
This is Venn – the Secure Enclave keeps your company-based apps, data and network safe and compliant. Venn secures remote work on any unmanaged or BYOD computer with a radically simplified and less costly solution than VDI.
- Centralizes administrative control over work data, application and peripheral use.
- Provides IT departments the robust control to remotely
enable, suspend, terminate or wipe at press of a button. - Ensures that all network access is policy-controlled
and guarded from accidental or malicious exfiltration, compromise or loss. - Significantly cuts costs and makes remote work a walk in the park for IT teams and employees. No need for remotely delivered apps – everything runs locally on the employees computer.
How Venn Keeps Work Inside a Secure Enclave

Launch Venn’s app
from any device
Venn kicks in and
automatically detects
work apps
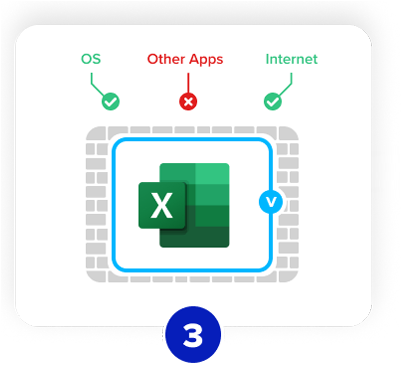
The blue border acts as
a firewall to safeguard
work apps and data
Work comfortably from any
device with guaranteed
compliance and regulations
We’re Venn – Fit for the New Era of
BYOD/BYO-PC
Enable Freedom
Without Compromise
Venn is the leading virtual desktop alternative for securing remote work on any unmanaged or BYOD computer. Venn’s secure workspace allows users to work securely, freely, anytime and anywhere. – that is our guarantee.
Take a tour of our Secure Enclave to see how Venn can
protect your company’s data and cut expenses.
Harness all of the Possibilities
On One Device
BYO-PC Workforce
Secure unmanaged and BYOD
on any PC or Mac.
Zero Trust Security
Isolate and protect work
data and applications.
Virtual Desktop Alternative
Eliminate complexity.

Securing Contractors
and Offshore Workers
Secure sensitive client assets
and meet compliance,
MDM for PCs
Control, Secure and Administer
policies on any BYOD laptop.
Work & Personal
on One Device
Employee productivity
improves business results.
Why We’re Different
Why Venn?

Security and Compliance
Guarding company data from
accidental or malicious
exfiltration, compromise or loss.

User Convenience
and Privacy
Enabling users to have a single
computer with clear separation
between work and private
personal uses.

Lower Cost
Reducing the cost and complexity
of buying, managing and securing
company-owned PCs and/or
virtual desktop infrastructure.

Full Control
Empowering robust administrative
control over work applications and
data including policies for network
access, peripheral use, copy-paste
and more.

Easy Deployment
Ability to integrate with
existing infrastructure.
Onboard/Offboard in
minutes.
Revolutionizing Secure BYO-PC
Key features needed to make remote and hybrid working successful for your employees.
 |
VDI, Cloud PCs, DaaS |
Browser-only | Company Managed |
|
|---|---|---|---|---|
| Security and Compliance
Provide a single point of access for all work apps, files, and websites. |
||||
| User Convenience and Privacy
Allows users to use a single computer for both work and life without impacting their user experience or performance in any way |
||||
| Cost
Helps cut down on HW and management costs for remote employee computing devices |
||||
| Control
Allows centralized security and IT policies and remote management of devices |
||||
| Easy Deployment
Self-service deployment and easy integration with 3rd party IT and security software |
||||
| Remote Work at Scale |


Venn makes work-from anywhere a real and secure option for our firm
The Future of Remote
Work is Here
Venn is the next-generation of safe workspaces –
empowering employees to use ONE PC for both
work and personal activities by creating a secure,
isolated enclave for company applications and data.
Fit to Secure BYO
and Managed Devices
Venn safeguards work files and data from
accidental or malicious exfiltration, compromise
or loss on any device. Protect sensitive records,
all with just a simple, quick deployment that can
integrate with any existing infrastructure.


A new freedom
of security with Venn


Productivity and compliance.
You can really have both
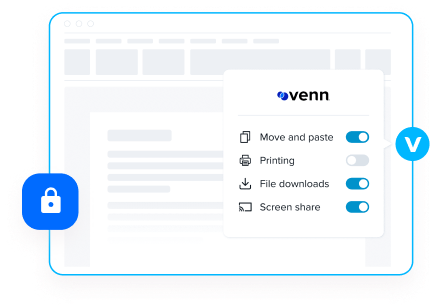
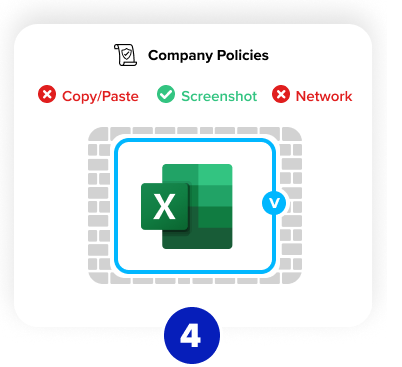
Control What the Users
Can and Cannot Do
With Venn, IT administrators have 100% control to
monitor work applications and data. This includes
managing policies for network access, copy-paste
features, screen capture, off-boarding and more.
Hop Onboard, You’re In Good Company
Over 700 highly regulated firms depended on Venn to empower their BYOD users.

Compliance with
Industry Standards
Venn ensures compliance with all current cybersecurity regulations which require development and implementation of mandatory policies, principles, standards and guidelines.